Dress to impress: Security risk analysis using bowties

The use of bowties as a risk assessment technique is a well-proven method. But whilst commonly used in the assessment of safety risks, is it a suitable tool for the assessment of security risks? Can bowties address the full scale of security threats?
Security threats can appear on vastly different scales, against an almost unlimited list of targets, employ a bewildering array of attack vectors and achieve staggeringly diverse consequences.
Scales can range from global cyber security attacks on international networks, to regional-level conflicts, to targeted terrorist or criminal activity against organisations and individuals. Consequences can be equally wide-ranging, from widespread fear, terror and paralysis of networks to the theft of an individual’s personal data.
VIVE LA DIFFÉRENCE
Putting this into context, the key differences between safety and security risk assessment and management are:
- Basis of assessment – safety assessment reviews events on an accidental and random basis, whilst security assessment considers acts to be deliberate and intentional.
- Terminology – safety assessment identifies hazards with the potential to cause harm, whereas security risk assessment starts with a threat.
- Mitigation – safety measures typically consider mitigation to a predefined (often regulated) level of risk, whilst security measures mitigate risks to meet the organisation’s risk appetite, sometimes making it hard to decide when sufficient security mitigations are in place.
- Understanding the risk – a safety risk usually acts within a set of identified parameters (e.g. defined operations) and is inherently predictable, at least in principle. A security risk, delivered by a third party with their own agenda, able to choose from one of many options which can change over time, can be much less predictable with much less certain consequences, making the selection of effective barriers far more difficult.
APPRAISING BOWTIE
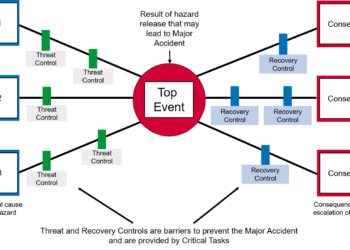
Clearly, any viable assessment technique must be able to cater for the entire range of security threats and risks, as well as its unpredictable nature. One strong candidate is the bowtie method. The risk management standard IEC 31010 describes a bowtie as:
‘A simple, diagrammatic way of describing and analysing the pathways of a risk…and reviewing controls…The focus of a bowtie is on the barriers between the causes and the risk, and the risk and the consequences.’
It is these qualities that make bowties so adaptable and suitable for the assessment of security risks at any scale and with the widest range of consequences.
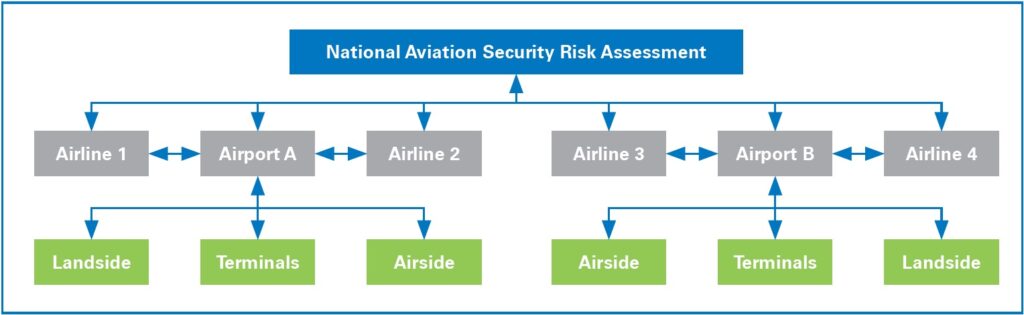
A good example is aviation security. A national aviation security agency could conduct a security risk assessment using bowtie at the national level, and then pass these risks down to the entity level (e.g. airport or airline) for detailed assessment and mitigation. Each entity can assess its risks at the appropriate level, and pass its mitigations up to the national level. Bowties at each level can link into the level above and below, so that a coherent picture of security is established (see Figure 1).
But what further advantages does the use of bowties bring to the assessment of security risks? Three distinct strengths are:
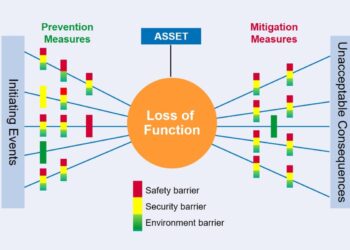
Strength 1. Bowties focus the attention on controls (barriers) that are supposed to be in place.
A bowtie is very powerful at showing on the same diagram:
- Threat priorities – which threats are most important and should be addressed first.
- Consequence categorisation – which consequences could deliver the worst outcome.
- Barrier criticality – which barriers are the most crucial for mitigating the threats or their consequences.
- Barrier effectiveness – which barriers are actually effective and those that are not.
The combinations of these attributes can be used to prioritise the focus of effort or to drive a maintenance programme. An example of an aviation security bowtie for an airport is illustrated in Figure 2.
Figure 2 – Aviation security bowtie example
Strength 2. Bowties do not need a high level of expertise to be understood.
Security impacts all personnel in an organisation and a complicated assessment technique can be unhelpful. A simple technique that can be used and understood by everyone is greatly beneficial and keeps the assessments alive and useful.
The bowtie technique stimulates debate and is particularly well-suited to brainstorming events.
Strength 3. A bowtie gives a clear pictorial representation of the problem.
This is probably the greatest strength of a bowtie as it enables a full assessment of each risk. In the example in Figure 2, a visual re view of the airport’s security bowtie would indicate that the barriers are effective against both a terrorist bomb onboard an aircraft, which is the highest threat priority, and also against the worst consequence category of loss of life. The barriers against cyber-attack on the other hand are poor and insufficient, meaning that the airport remains vulnerable to the threat and the consequences, whilst the barriers for protestor activity appear to deliver more mitigation than is required.
From such a review, the airport can redirect its resources to deliver balanced and proportionate mitigation against each threat.
CONCLUSION
The assessment and management of security risk poses a unique challenge, given the scope, uncertainty and evolution of the associated threats. Bowtie analysis provides an extremely versatile and informative risk assessment technique that is straightforward to adapt to meet this challenge.